After a conversation with Microsoft where we were discussing users who are having issues signing in with B2B, I thought it would be good to share what I’ve learned.
When you using Azure AD as the identity provider for your applications and are using B2B (Guest) accounts to allow external users to access your applications, you will at some point encounter users who are unable to sign in. There are a number of issues that could arise and the information against the users profile will help you to diagnose where the problem is likely to be.
If you go to the Azure AD portal and search for the user by their email address and click through to their profile, I’ve highlighted a number of areas of interest.
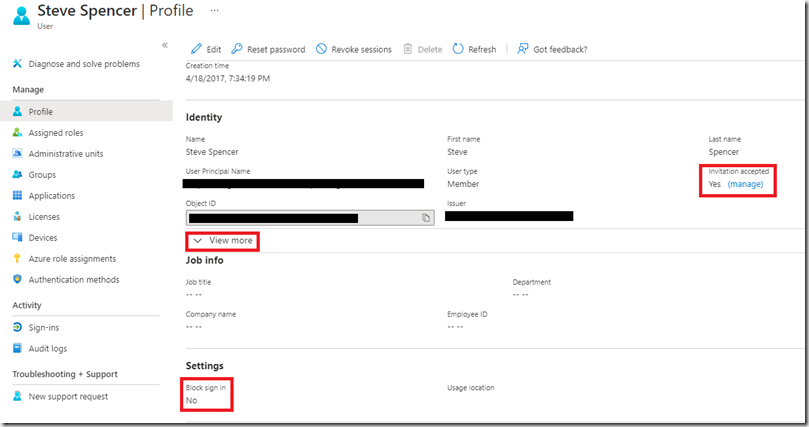
The box on the right shows whether the user has accepted the invitation or not. The bottom box shows whether the user has been blocked access to your Azure AD. Maybe they were a user previously on a different application and for some reason their access has been blocked. If this is the case then it is best to look at the Groups and Applications that the user is already assigned to before you unblock the user.
If the user has accepted the invitation then the final box (“View more”) will give you some useful information. Expanding the box will show you where the users B2B account originates:

This one shows the user has a Microsoft account.
The values can be:
- Invited User: This user has been invited but has not yet redeemed an invitation.
- External Azure Active Directory: This user is homed in an external organization and authenticates by using an Azure AD account that belongs to the other organization.
- Microsoft account: This user is homed in a Microsoft account and authenticates by using a Microsoft account.
- Windows Server Active Directory: This user is signed in from on-premises Active Directory that belongs to this organization.
- Azure Active Directory: This user authenticates by using an Azure AD account that belongs to this organization
Further details can be found here
The source can help you to tailor your response to the user. For example, if the Source shows External Azure Active Directory, you know that the user is signing in with their corporate account and if they are having issues signing in then it is likely to be an issue at their end. If it shows Microsoft Account then they need to use the credentials they use to access their Hotmail, One drive or personal computer (if they have it connected to their Microsoft Account) and you can point them to the relevant pages for assistance.
Once they have signed in correctly they may still have issues accessing your application. You would need to look at the configuration of the application, Conditional Access (Note, conditional access could be an issue at their end, if their corporate IT have blocked B2B access at their end for example), group configuration etc.
I found that being able to identify where the users credentials are sourced meant that I could provide a far better support response to my customers and this resolved a lot of the issues.